What's New
-
The verification results page for the Microsoft Security Baseline and Microsoft 365 Apps Security Baselines now displays the correct current value when a setting is non-compliant, so you can see exactly why it's non-compliant and which existing value causes the issue.
-
The Protect page → Device Usage Intents section now permits only one intent to be selected at a time, matching the intended usage and removing ambiguity.
-
The Device Usage Intents preview ListView on the Protect page now lets you remove individual security measures from the preview before pressing Apply, giving you finer control over what gets applied. Items can be deleted in two ways:
- Right-click (or Tap + Hold) a row and choose the delete option.
- Swipe left on touch devices — a smooth animation and deletion motion will remove the item from the ListView.
-
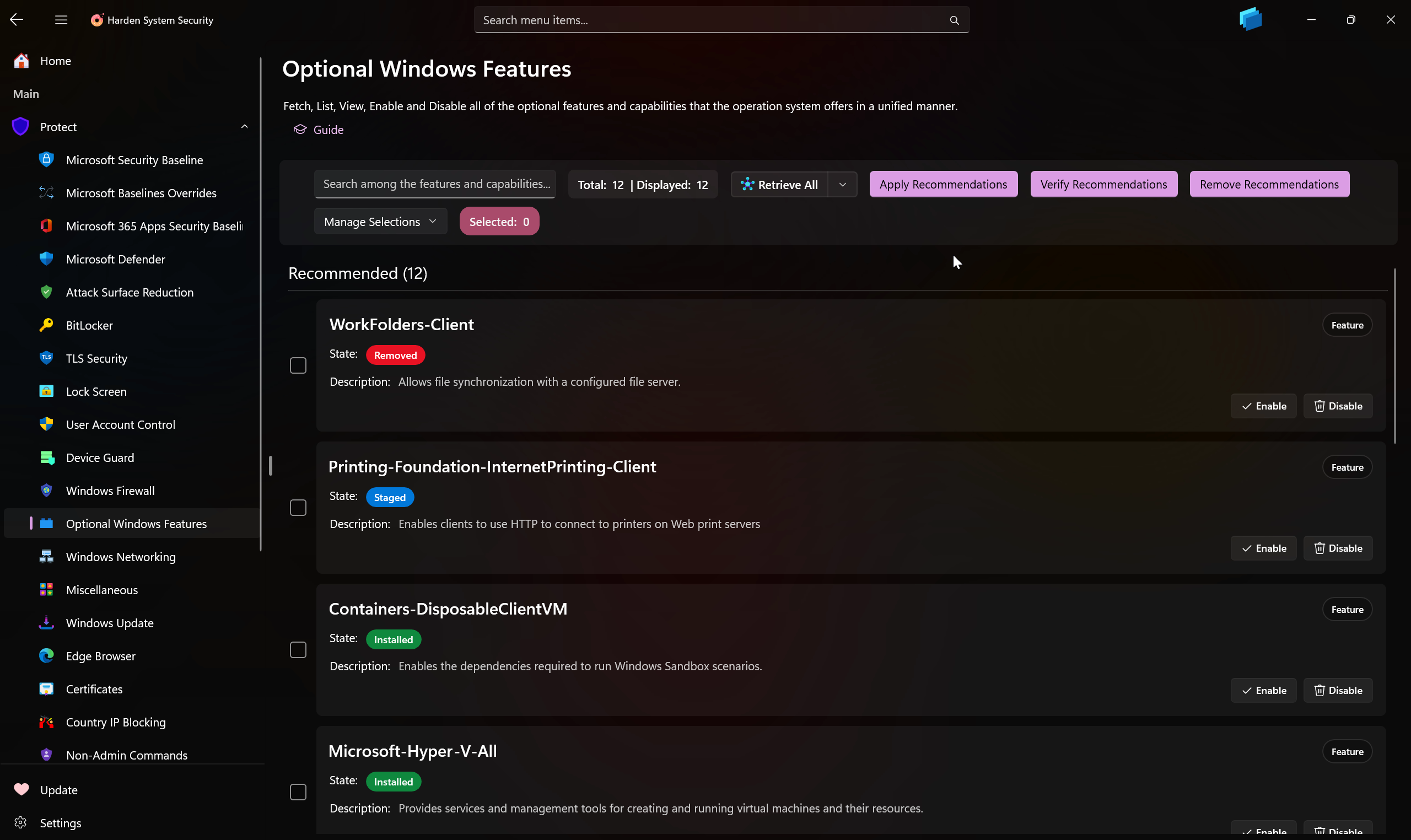
On the Optional Windows Features page, each feature/capability now shows a per-item progress bar while verifying, removing, or applying, so you can see realtime progress for that specific item. Realtime progress is no longer written to the logs as text, avoiding many unnecessary log entries.
-
Also on the Optional Windows Features page, the app automatically scrolls the ListView to the currently active item during removal or apply operations, making it easy to track that item's realtime progress without manual scrolling.
-
Again on the Optional Windows Features page, added a new group to the ListView called "Network Adapters", it groups and displays all currently installed network adapter drivers that come by default with the operating system. This allows you to easily identify and remove unnecessary network adapters that you don't need/use, freeing up disk space and potentially reducing attack surface.
-
Expanded the scope of the app during verifications of the security measures applied via Group Policies. Previously, they would only be verified and detected if they were applied via Group Policy, but beginning with this update, they will be detected via registry keys as well. This improves the accuracy of the verification and compliance results by widening the scope of detection. This is only phase one of a multi-phased effort to detect policies applied via Microsoft Intune. Appropriate logs are generated accordingly. See the related community discussion.
-
Added extra detection logic for active TLS Cipher Suites in the TLS category.